In the complex financial landscape, a robust Know Your Customer (KYC) framework is not just a regulatory hurdle; it’s a bank’s primary defence against financial crime. For businesses and financial professionals, understanding the architecture of these policies is crucial for ensuring compliance and operational integrity. This guide demystifies this essential process, breaking down the core components into manageable, actionable insights. We will explore how modern banks kyc policies incorporates the following key elements to build a secure and compliant banking environment.
This article moves beyond the acronyms to provide a clear, practical overview of each stage. From initial customer identification and due diligence to sophisticated ongoing monitoring and risk assessment, you will gain a comprehensive understanding of how these elements work in unison. We will examine the specific procedures and technologies that financial institutions use to protect themselves, their customers, and the integrity of the global financial system against illicit activities.
Table of Contents
1. Customer Identification Program (CIP)
The Customer Identification Program (CIP) is the foundational pillar upon which all other KYC and Anti-Money Laundering (AML) efforts are built. As a key element of banks’ KYC policies, its primary function is to form a reasonable belief that the bank knows the true identity of each customer. This non-negotiable step occurs before or during account opening and involves collecting and verifying essential identifying information.
A robust CIP requires verifying a customer’s identity through reliable, independent source documents, data, or information. This typically includes a combination of documentary evidence, like a passport or Aadhaar card, and non-documentary methods, such as cross-referencing information with credit bureaus or public databases. For example, major banks like HSBC implement global CIP standards tailored to local documentation requirements, ensuring consistent yet context-aware verification across all regions.
Implementing an Effective CIP
To ensure your CIP is both compliant and efficient, consider these practical steps:
- Risk-Based Verification: Implement a tiered approach. A low-risk customer opening a basic savings account might require standard document verification, while a high-net-worth individual might need enhanced due diligence, including biometric checks.
- Automate Document Processing: Use automated document scanning and optical character recognition (OCR) technology to extract information quickly, reducing manual errors and processing time.
- Maintain Updated Document Lists: Regularly review and update the list of acceptable identification documents to align with regulatory changes and prevent the use of outdated or fraudulent IDs.
The following infographic summarises the core components of a standard Customer Identification Program.
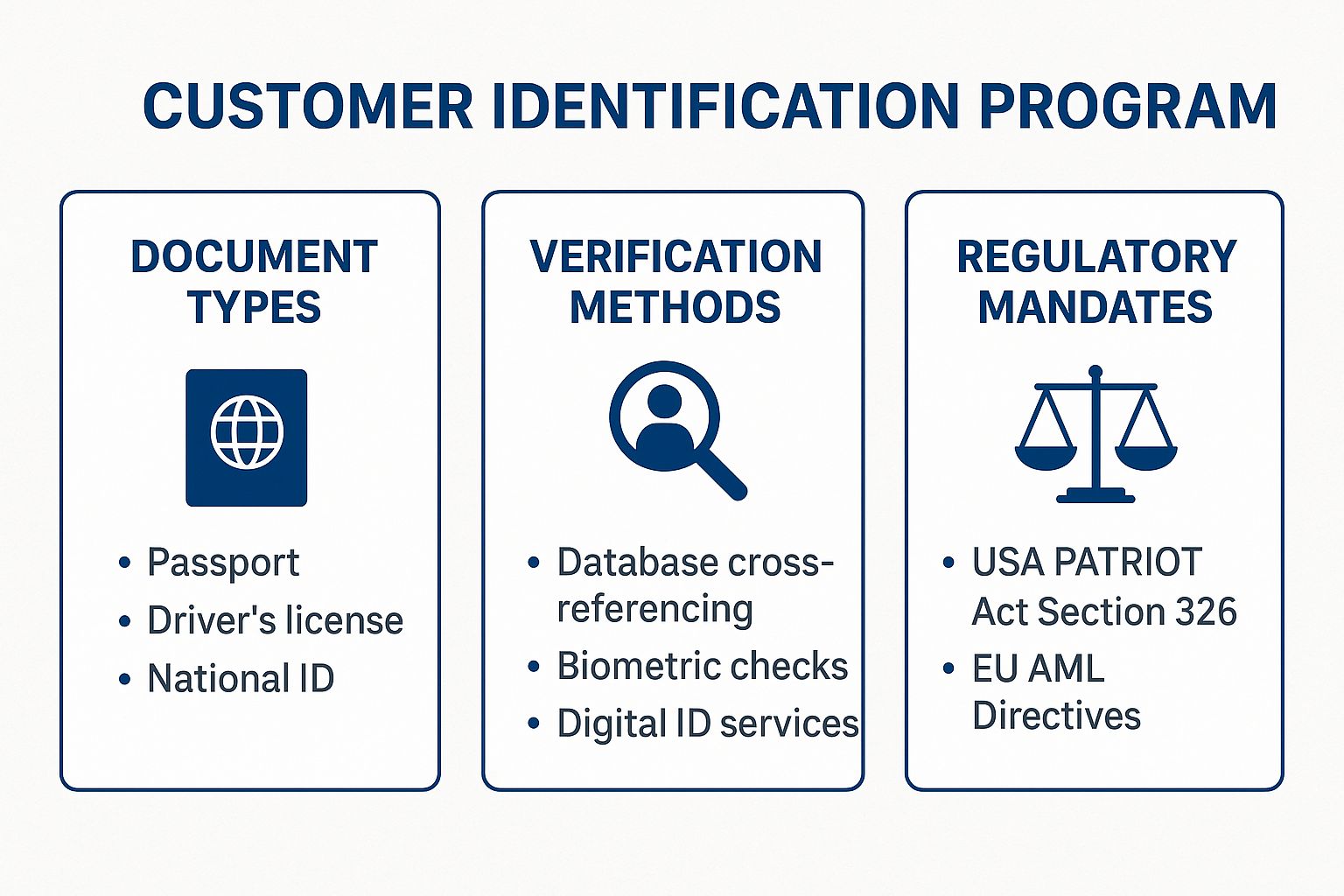
This visual highlights how a CIP integrates document types, modern verification methods, and overarching regulatory mandates to create a cohesive identity verification framework. By mastering these components, financial institutions can establish a strong defence against illicit activities from the very first interaction. You can learn more about comprehensive identity verification solutions.
2. Customer Due Diligence (CDD)
Customer Due Diligence (CDD) is a critical ongoing risk assessment process that moves beyond the initial identity verification of CIP. As one of the core elements banks’ KYC policies incorporates, its primary goal is to understand the nature and purpose of a customer’s relationship with the bank. This involves gathering information on business activities, anticipated transaction patterns, and the source of funds to build a comprehensive risk profile.
A thorough CDD process allows banks to assess and categorise customer risk levels, which determines the appropriate degree of monitoring required. For instance, Standard Chartered employs a risk-based CDD approach, applying enhanced procedures for customers linked to high-risk jurisdictions or industries. Similarly, Deutsche Bank integrates its CDD framework with real-time transaction monitoring systems to detect unusual activity that deviates from the established customer profile, enabling a proactive response to potential financial crime.

Implementing an Effective CDD
To ensure your CDD process is robust and scalable, consider these practical steps:
- Develop Clear Risk-Rating Criteria: Establish and document objective criteria for classifying customers as low, medium, or high risk based on factors like occupation, geography, and transaction types.
- Automate Routine CDD Processes: Use technology and AI-powered tools, like those implemented by Citibank, to automate the collection and analysis of customer data, freeing up compliance teams to focus on high-risk cases.
- Establish Periodic Review Cycles: Implement a schedule for reviewing customer information, with the frequency determined by their risk level. High-risk customers should be reviewed more often than low-risk ones.
3. Enhanced Due Diligence (EDD)
Enhanced Due Diligence (EDD) is an elevated level of scrutiny that banks’ KYC policies incorporate for customers identified as high-risk. While standard due diligence applies to all customers, EDD is a necessary intensification designed to mitigate heightened risks associated with specific profiles, such as politically exposed persons (PEPs), clients from high-risk jurisdictions, or those with unusually complex business structures. Its core purpose is to gain a deeper understanding of the customer’s identity, source of funds, and the nature of their transactions to prevent money laundering and terrorist financing.
This advanced verification process involves more comprehensive investigation and more frequent, intensive monitoring of account activity. For instance, global banks like UBS often require board-level approval for certain high-risk relationships, while others like Bank of America implement mandatory annual reviews for all PEP accounts. These measures ensure that the bank’s relationship with high-risk customers is well-documented, understood, and continuously monitored for any suspicious behaviour.

Implementing an Effective EDD
To integrate a robust EDD framework, financial institutions should focus on clear procedures and specialised resources:
- Establish Clear Triggers: Define specific, non-negotiable criteria that automatically trigger an EDD review, such as a customer’s presence on a PEP list or transactions involving jurisdictions flagged by the Financial Action Task Force (FATF).
- Invest in Specialised Training: Equip compliance teams with advanced training to handle complex EDD cases, enabling them to analyse intricate corporate structures and identify hidden beneficial owners effectively.
- Document All Decisions: Meticulously record every step of the EDD process, including the rationale behind risk assessments and approvals. This creates a defensible audit trail for regulators.
4. Ongoing Monitoring and Transaction Screening
Ongoing Monitoring and Transaction Screening is the dynamic surveillance component of KYC, extending due diligence beyond the initial onboarding phase. As a critical element in how banks’ KYC policies incorporate ongoing compliance, its purpose is to continuously analyse customer activities to detect suspicious patterns, unusual transactions, and potential sanctions violations in real-time. This process ensures that the bank’s understanding of a customer’s risk profile remains current and accurate over the entire relationship lifecycle.
A robust monitoring system involves scrutinising transactions against established rules and customer profiles to identify deviations from expected behaviour. For instance, JPMorgan Chase uses AI-powered monitoring that has successfully reduced false positives by 50%, allowing compliance teams to focus on genuinely high-risk alerts. Similarly, this continuous screening checks customer names and transaction details against updated sanctions lists and watchlists, preventing illicit funds from moving through the financial system.
Implementing Effective Ongoing Monitoring
To ensure your monitoring system is both effective and efficient, consider these practical steps:
- Calibrate Monitoring Rules: Regularly review and adjust your transaction monitoring rules and thresholds to reflect emerging money laundering typologies and minimise false positives.
- Implement Risk-Based Tiers: Apply different monitoring intensities based on customer risk levels. High-risk customers should be subject to more frequent and stringent screening than low-risk customers.
- Leverage Machine Learning: Employ machine learning and behavioural analytics to enhance detection accuracy, uncover complex illicit networks, and adapt more quickly to new threats than traditional rule-based systems.
5. Sanctions and Watchlist Screening
Sanctions and Watchlist Screening is a critical, ongoing process within KYC policies, designed to prevent financial institutions from conducting business with prohibited individuals or entities. This element involves systematically checking customers, transactions, and business relationships against government-issued sanctions lists, law enforcement watchlists, and internal risk databases. It serves as a real-time defence against facilitating terrorist financing, money laundering, and other financial crimes.
This screening is not a one-time check but a continuous obligation. For example, ANZ Bank implements real-time screening for all payment transactions, while Wells Fargo screens against over 600 sanctions and watchlists globally. These robust systems ensure that banks kyc policies incorporates the following key elements of vigilance, actively identifying and blocking illicit activities before they can penetrate the financial system. For effective screening, banks must monitor regulatory updates, such as FINCEN’s alerts on sanctions evasion, to stay ahead of evolving threats.

Implementing an Effective Screening Process
To ensure your screening process is both compliant and highly accurate, consider these practical steps:
- Use Advanced Matching Algorithms: Implement fuzzy logic and advanced algorithms to reduce false positives and identify non-obvious name variations. Barclays, for instance, uses AI-enhanced screening that successfully reduced false positives by 40%.
- Establish Clear Escalation Procedures: Define a clear, documented process for investigating and resolving potential matches, including roles, responsibilities, and timelines for escalation to senior compliance staff.
- Implement Quality Control for Lists: Regularly audit and update your sanctions lists and internal watchlists to ensure they are current, accurate, and comprehensive, removing outdated entries and adding new ones promptly.
6. Risk Assessment and Rating Systems
Risk Assessment and Rating Systems are structured methodologies that banks use to evaluate and categorise customers based on their potential risk for money laundering or terrorist financing. This key element of banks’ KYC policies moves beyond simple identity verification by assigning a risk level to each customer, which then dictates the intensity of ongoing monitoring and controls. These systems analyse multiple factors, such as customer type, geographic location, and transaction patterns, to create a holistic risk profile.
A powerful risk rating system enables banks to allocate compliance resources more effectively, focusing enhanced scrutiny on high-risk accounts while streamlining processes for low-risk ones. For instance, Goldman Sachs utilises advanced machine learning models incorporating over 200 risk variables to achieve precise customer segmentation. Similarly, ING Bank employs behavioural analytics to adjust customer risk ratings in real-time based on transactional activity, ensuring the risk profile remains current and dynamic.
Implementing an Effective Risk System
To build a robust and compliant risk assessment framework, consider these practical steps:
- Include Diverse Risk Factors: Go beyond standard demographics. Incorporate transactional behaviour, business industry, political exposure, and negative media screening to create a more accurate and nuanced risk score.
- Validate Models Regularly: Continuously test your risk models against actual outcomes and historical data to ensure their predictive accuracy. This validation process helps identify and correct any model decay over time.
- Establish Governance for Overrides: Implement strict, documented procedures for any manual overrides of system-generated risk ratings. These controls should require senior approval and clear justification to maintain integrity.
For banks to effectively assess and manage these customer-associated risks, it is vital to have a clear framework. Further insight into this topic can be gained by understanding the five stages of risk management. Integrating these systems is crucial for fintech and banking compliance. You can explore more on how technology is shaping risk management in the fintech sector.
7. Record Keeping and Documentation Requirements
Record keeping is the evidentiary backbone of any KYC policy, providing the auditable proof of a bank’s due diligence efforts. This element involves the systematic maintenance and retention of all customer identification data, transaction histories, and related compliance documentation. Its core purpose is to ensure that banks can demonstrate adherence to regulatory mandates, support internal audits, and assist law enforcement with investigations when required.
Effective documentation is non-negotiable, as it underpins the entire KYC framework. Leading institutions have transformed this from a simple storage task into a strategic capability. For instance, Morgan Stanley maintains digital records with 24/7 availability for regulatory access, while TD Bank implements automated retention policies with secure deletion processes to manage the data lifecycle effectively. These practices show how robust banks’ KYC policies incorporates the following key elements for comprehensive data management.
Implementing an Effective Record-Keeping System
To ensure your record-keeping practices are compliant and secure, consider these practical steps:
- Automate Lifecycle Management: Implement automated retention and deletion policies based on regulatory timelines to prevent accidental data loss or non-compliant storage.
- Use Secure, Encrypted Storage: Store all KYC data in secure, encrypted systems, both at rest and in transit, to protect sensitive customer information from unauthorised access.
- Ensure Rapid Accessibility: Organise records so they are easily and quickly retrievable for audits, regulatory examinations, or law enforcement requests without compromising security protocols.
8. Regulatory Reporting and Suspicious Activity Reporting (SAR)
Regulatory Reporting, particularly the filing of Suspicious Activity Reports (SARs), serves as a critical communication channel between financial institutions and law enforcement. As a key element in how banks’ KYC policies incorporate the following key elements of AML, this process formalises the reporting of transactions or activities that raise red flags for potential illicit conduct. It is the mechanism through which banks alert authorities to potential money laundering, terrorist financing, or fraud.
A strong SAR framework involves not just filing reports but doing so with accuracy and timeliness. For instance, HSBC now uses sophisticated AI to prioritise investigations and improve the quality of its SAR filings, ensuring that the most critical alerts are escalated efficiently. This proactive reporting is mandatory and acts as a vital intelligence source for financial crime investigators, making it a cornerstone of a bank’s contribution to national security.
Implementing an Effective SAR Process
To ensure your reporting framework is compliant and effective, consider these practical steps:
- Establish Clear Criteria: Define and document specific thresholds and red flags that trigger a SAR investigation and subsequent filing. This removes ambiguity and ensures consistency.
- Provide Continuous Training: Regularly train staff on identifying new and evolving suspicious activity indicators, such as unusual crypto transactions or complex trade-based money laundering schemes.
- Implement Quality Control: Create a mandatory peer or supervisory review process for all SAR filings before submission. This minimises errors and enhances the report’s utility for law enforcement.
This reporting function transforms a bank’s internal monitoring efforts into actionable intelligence for regulators. By mastering SAR procedures, institutions fulfil a core compliance duty and actively participate in the broader fight against financial crime. You can learn more about robust compliance frameworks.
8-Point KYC Policy Elements Comparison
| Item | Implementation Complexity | Resource Requirements | Expected Outcomes | Ideal Use Cases | Key Advantages |
|---|---|---|---|---|---|
| Customer Identification Program (CIP) | Moderate; involves document and database verification | High; manual and automated verification tools | Verified basic customer identity; fraud prevention | Account opening, initial customer onboarding | Prevents identity fraud, regulatory compliance, audit trails |
| Customer Due Diligence (CDD) | High; requires risk assessments and ongoing updates | Intensive; skilled personnel and technology required | Risk-based customer profiles; detection of suspicious activity | Risk categorization, monitoring medium-risk customers | Enables risk-based management, reduces false positives |
| Enhanced Due Diligence (EDD) | Very high; deep investigations, senior approvals needed | Very high; specialized teams and extended monitoring | Strong financial crime prevention for high-risk clients | High-risk customers, PEPs, complex ownership | Provides stronger compliance, reduces regulatory penalties |
| Ongoing Monitoring and Transaction Screening | High; requires real-time systems and advanced analytics | High; significant technology investment and tuning | Rapid detection of suspicious transactions | Continuous transaction surveillance, AML compliance | Enables automation, audit trails, and prompt alerts |
| Sanctions and Watchlist Screening | Moderate to high; multiple list integrations and updates | Moderate to high; systems for screening and false positive management | Prevents dealings with prohibited entities | Transaction and customer screening against sanctions | Reduces legal risks, automated compliance, detailed audits |
| Risk Assessment and Rating Systems | High; model development and ongoing validation required | High; data management and analytics expertise needed | Accurate risk ratings for resource allocation | Customer risk evaluation, regulatory reporting | Consistent risk framework, supports risk-based approach |
| Record Keeping and Documentation | Moderate; secure storage and retention policies required | Moderate; IT infrastructure and compliance management | Audit-ready customer and transaction records | Regulatory examinations, compliance audits | Ensures regulatory compliance, legal protection, audit trails |
| Regulatory Reporting and SAR | High; requires automated systems and quality assurance | High; trained staff and secure reporting platforms | Timely and accurate suspicious activity reports | Reporting suspicious transactions to authorities | Fulfills legal obligations, aids law enforcement, protects bank |
Integrating KYC Elements for a Stronger Compliance Posture
Mastering compliance in today’s financial landscape requires more than just ticking boxes. As we’ve explored, a robust framework is built on how banks’ KYC policies incorporate the following key elements: a rigorous Customer Identification Programme (CIP), thorough Customer Due Diligence (CDD), and vigilant Enhanced Due Diligence (EDD) for high-risk profiles. These foundational pillars work in concert, not in isolation. They are designed to create a comprehensive understanding of each customer, forming a resilient first line of defence against financial crime.
The effectiveness of this defence, however, depends on its dynamism. Ongoing monitoring, real-time transaction screening, and constant cross-referencing against sanctions lists are not static activities but continuous, evolving processes. They ensure that a customer’s risk profile remains accurate over time. This proactive approach is underpinned by a sophisticated risk assessment system and meticulous record-keeping, which are crucial for both internal governance and regulatory scrutiny. Ultimately, the ability to identify and report suspicious activities through SARs is what transforms a passive policy into an active, protective mechanism.
For any organisation, integrating these components into a seamless workflow is the ultimate goal. The value lies in creating a cohesive ecosystem where each element informs and strengthens the next, moving from a reactive, checklist-based approach to a proactive, risk-based strategy. This synergy not only ensures regulatory adherence but also builds a foundation of trust and integrity with customers and regulators alike. By understanding how these parts connect, businesses can build a compliance posture that is both resilient and adaptable to future challenges.
Ready to fortify your own onboarding and verification processes? While you navigate the complexities of compliance, let SpringVerify handle the heavy lifting of background and identity verification with speed and precision. Secure your business and build trust from the outset by integrating our instant, reliable KYC solutions.






